Technology surrounds us, and a little piece of tech black magic lies in your pocket that makes mobile communication possible: the SIM card. Ever wondered how this tiny chip connects you to the world? If so, you’re not alone. Be it making phone calls, sending a text, or endless scrolling on your favorite social application, your SIM card is working hard in the background. So, here’s the story of SIM cards, how they work, and the basics of mobile authentication.
SIM Card As A Mobile Network Element
Upon entering the end of SIM, we see that SIM means Subscriber Identity Module. It’s a small integrated circuit placed in your mobile phone that functions as your digital ID card. This identification is specific to you and tells your mobile carrier that it’s you attempting to access their network.
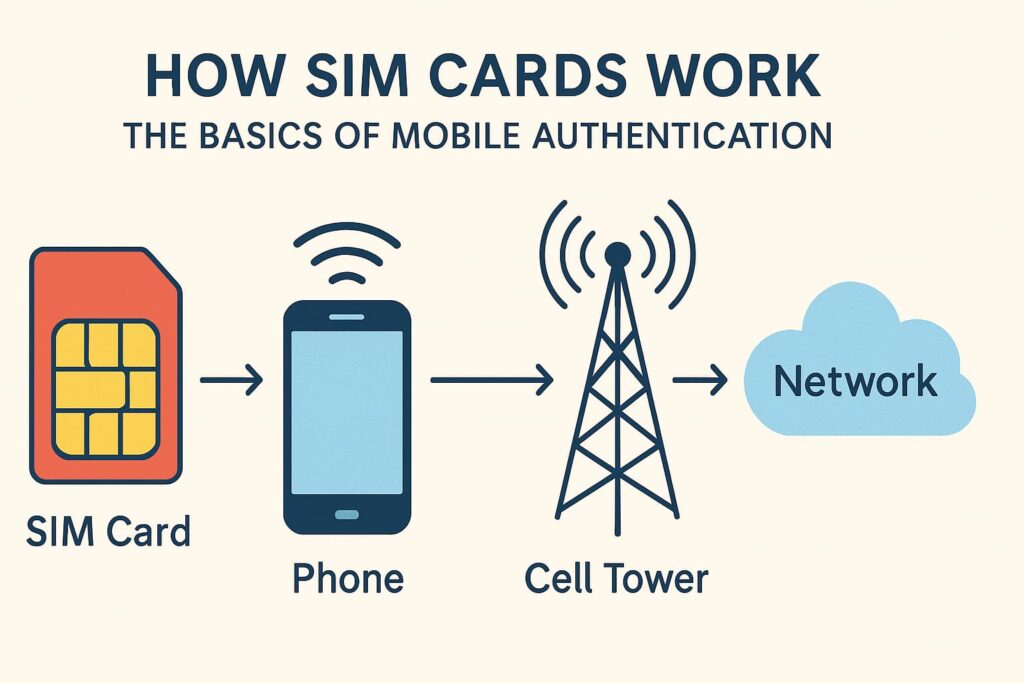
But that’s only the tip of the iceberg. Many important details, such as your International Mobile Subscriber Identity (IMSI) and authentication keys are stored on a SIM card. This information is used by the network to reaffirm your identity and provides you access to voice, data and SMS services.
So much so that to validate who is using the SIM cards, the Indian Government brought in tafcop.dgtelecom.gov in, a portal to check how many sim cards are there against a user and link them with an identity. This also plays an important role in curbing fraud and preventing the use of unauthorised SIM cards, which adds an extra safety layer for subscribers.
Authentication on Mobile Communication
In the mobile world, that’s exactly the role your SIM card serves. It verifies your identity whenever your phone tries to connect to a cell tower. This process verifies that you are a legitimate user and prevents such misuse of the network.
Here, it is important to note that if you face connected issues, especially if mobile service providers have connected you to connections that were not authorized by you, or you suspect that your identity is compromised using mobile services, you can contact Tafcop customer care. They can help you regain control of your mobile identity and keep your data secure.
A Peek Inside the SIM Card
Let’s demystify the tech! SIM cards are actually small chips that have a little bit of memory and processing power. Here’s what’s stored inside:
- The IMSI (International Mobile Subscriber Identity): Your identifier to the mobile network (long-term, therefore, a bit insecure).
- Authentication Key (Ki) — A secret code known only by your network provider.
- SMS Messages: Relatively few texts.
- Contacts: Phone numbers and names stored in the SIM.
- Loc Net Info: And the shit has handled temporary data, local towers.
Whenever your phone powers up, it reads the SIM and transmits encrypted data to the network. If the credentials are correct, you are granted access like a key entering a lock.
You can check a similar post on SIM: Best ways to get SIM card details in 10 minutes
Types of SIM Cards in Use Today

SIM cards have gone through many iterations and changed in both function and in size over the years:
- Full-size SIM: The original form factor, now largely obsolete.
- Micro SIM: A miniaturised version used in many older smartphones.
- Nano SIM: The current size in widespread usage throughout most new devices.
- eSIM (Embedded SIM): A digital SIM embedded inside your phone — no card to insert or remove.
All variations operate the same, but are tailored for various device specifications. The eSIM, in particular, is a game changer when it comes to connectivity, providing users the ability to change carriers without having to swap cards.
How Do SIM Cards Provide Security?
You need security in every digital activity, not just as a feature but as a basic part of using any mobile service. This is where SIM-based mobile authentication plays a role. It uses encrypted methods to protect your calls, data, and identity by verifying through your mobile network. Here’s how it works:
- Challenge-Response Process: Upon connection, the network sends a challenge. Your SIM replies with its authentication key.
- Push Notifications: Usually sent for secured transactions on the mobile number associated with your SIM.
- End-to-End Security: Apps like WhatsApp treat your mobile number as a base to encrypt messages.
Given all these constituencies involved in the security and safety of the SIM card, is it any wonder a SIM card has become a well-trusted base of digital identity?
SIM Cloning and Fraud: SIM card cloning and fraud
At the same time, technology also invites digital tricksters. This type of attack is called SIM cloning, in which someone simply copies your SIM data so that they can steal your calls & texts, along with other details. Always be alert if:
- Then suddenly you hear nothing more, radio silence.
- Your phone says “No Service,” but others are connected.
- You have charges you didn’t know about on your mobile bill.
As for one basic way to stay safe, keep your mobile account locked down with a strong PIN and don’t share any personal information online. You can also monitor using government tools such as Tafcop to look out for SIM activity under your ID.
For Now, Why SIM Cards Are Here to Stay
Maybe not, despite the chatter about how new-fangled systems such as virtual SIMs and cloud-based communication are threatening it, SIM cards aren’t going anywhere. Their mix of physical portability and secure encryption remains essential for global mobile infrastructure.
Although eSIM adoption is on the rise, swathes of users will still see hundreds of millions of traditional SIM cards through the rest of the 2020s. They are still a critical link in the mobile chain, from rural areas to urban centers.
The Future: From SIM to eSIM and Beyond
SIM technology has a bright future ahead. As mobile devices grow more intelligent and interconnected, expect innovations to include:
- PIN Code: Your smartphone becomes a secure container for your data.
- Preparing for 2023: What Are IoT SIM Cards and Why Are They Useful?
- SIMeGOV: Empowering e-Governance & mobile banking with SIM Secure Identity Management
In a time when your phone is your wallet, your identity, and your communicator, the SIM tech is rapidly innovating to keep pace.
How SIM Cards Work: An Introduction to Mobile Authentication
So, let me break it down: a SIM card is not just a chip; it is a digital handshake between you and your mobile network. It authenticates, secures and links you to the digital world seamlessly.
If you know how SIM cards work, it not only helps you appreciate your smartphone more but also gives you the tools to protect your mobile identity in a digital world. Whether you’re looking at your numbers on Tafcop or calling up Tafcop customer care for help, knowledge is your best line of defence.